
Cyber Risk Services
Cyber risk solutions that help you build trust with your clients and partners.
The foundation of a sound information technology strategy begins with having proper governance in place.
Without an established set of objectives, performance targets, and policies that your employees, third parties, and stakeholders adhere to, it's impossible to manage risk levels for implementing and managing technology, especially in the event of a system outage or malicious attack.
Today, your boards, clients, vendors, and insurers all have expectations of proper governance over your technology stack. Bringing in a trusted advisor to assess and craft a strategic improvement program is essential to implementing and maintaining meaningful IT practices.
Core Practice Areas
Learn more about each of our core practice areas and the services we offer to help you maintain compliance and safeguard your sensitive data, employees, and organization.
A Multidisciplinary Team Built for Real Business Challenges
Our Cyber Risk Services are powered by a robust combination of Security Architects, Technologists, and Governance Advisors working seamlessly to align your security posture with business objectives, regulatory demands, and emerging threats.
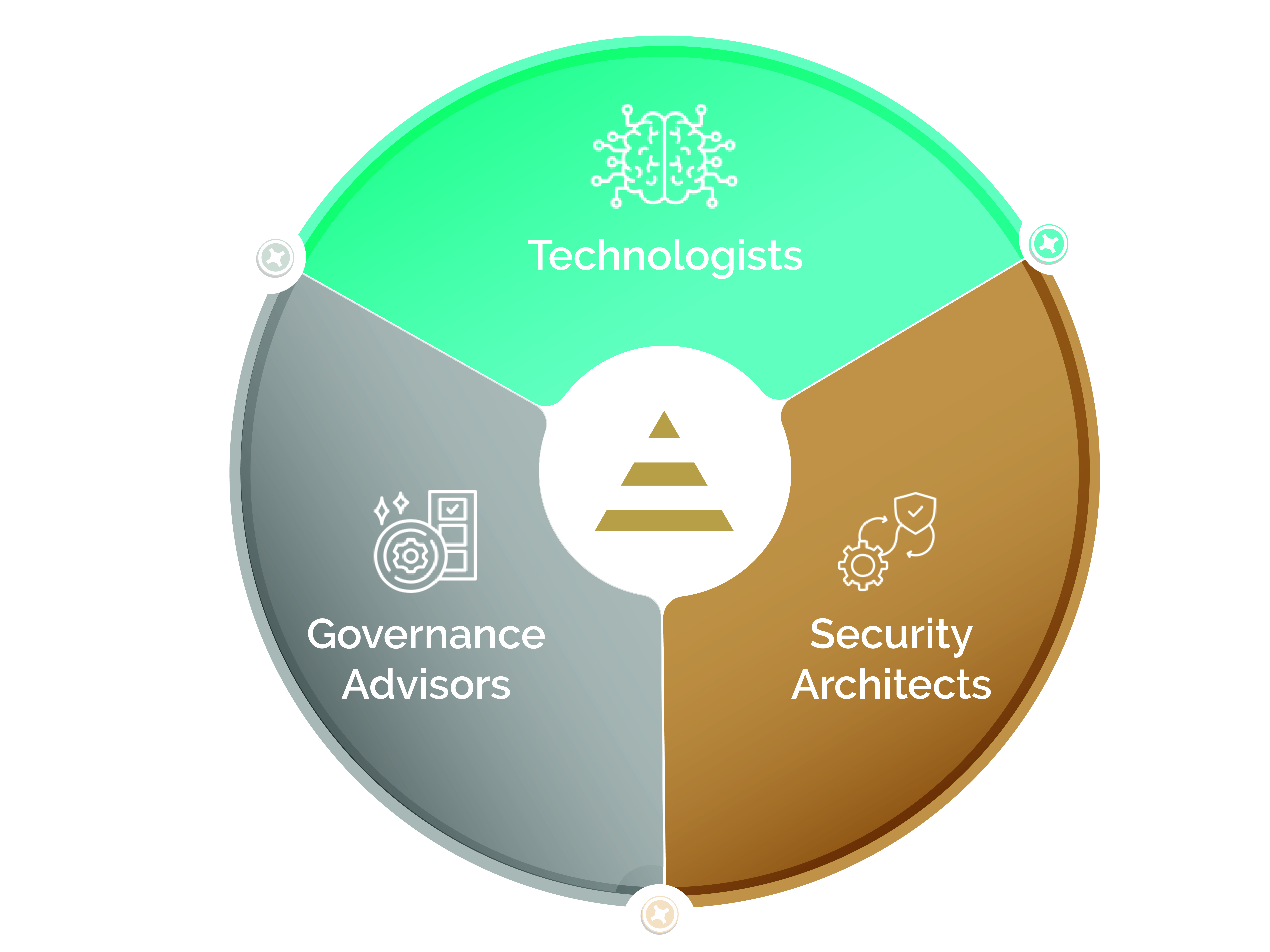
Our multidisciplinary team includes:
- Technologists: Define risk appetite, develop board‑level roadmaps, and align security with business goals
- Security, System & Network Engineers: Architect, configure, and continuously monitor your infrastructure
- Web Application & Cloud Security Specialists: Harden code, APIs, and cloud environments against modern threats
- Certified Ethical Hackers: Execute red‑team exercises and penetration tests to validate controls
- CMMC Registered Practitioners: Guide you through CMMC Level 1 & 2 readiness and certification
- HITRUST Assessors: Lead HITRUST CSF implementation, gap assessments, and audit support
- Governance Advisors: Interpret and apply regulations (SOX, PCI, GDPR, HIPAA, etc.) to your unique environment
- IT Internal Auditors: Identify, assess, and mitigate IT risks through rigorous audit practices
Meet the Team
A Deeper Look into Our Core Practice Areas
IT Risk
Today, security threats come at you from every angle, data point, and weak link. How well you prepare is an indication of how well you can mitigate future risks. Our experienced team of IT risk specialists can help you find even the smallest gaps while guiding you to help your organization follow the established risk protocols continually.
Our IT Risk Services
- IT Audit Co-sourcing Services
- Third Party Risk Management and Vendor Security
- Business Continuity & Disaster Recovery
- IT Governance and IT Risk Management
- Artificial Intelligence Governance
Cybersecurity
Our dedicated professionals understand that every organization has different needs, yet all require strong cybersecurity processes to adequately identify, assess, and mitigate cybersecurity threats. We work to efficiently strengthen your cybersecurity posture by monitoring current systems and internal controls, implementing innovative processes, and evaluating current systems against framework controls.
Our Cybersecurity Services
- NIST 800-53, 800-171, and the NIST Cybersecurity Framework
- CIS Critical Security Controls
- Vulnerability Assessments & Penetration Testing
- Web Application Security
- Network Security
- Incident Response & Digital Forensics
- Ransomware Readiness
- Cyber Risk Tabletop Exercises
Data Privacy
Our team manages an inventory of personal information in your environment and identifies how your current process involves the collection, use, sale, and sharing of that information. After identifying gaps between existing processes and applicable regulatory requirements, we help you develop and monitor your privacy compliance program and provide ongoing privacy program management
Our Data Privacy Services
- Data Privacy and Governance
- Privacy Technology Adoption
- Data Mapping and Data Tagging
- Data Protection
- Data Loss Prevention (DLP)
IT Compliance
With a long history in providing audit and tax services to our clients, we are focused on risk and compliance. Our cyber risk professionals are highly versed in creating IT governance standards specific to your organization's industry. Using proprietary software and innovative tools, we help you develop and maintain IT governance protocols to meet the highest levels of compliance and keep pace with evolving regulations each year.
Our IT Compliance Services
- SOX 404 ITGC & App Controls
- SEC Cyber Reporting Requirements
- PCI Compliance
- CMMC L1 and L2 Readiness
- HITRUST CSF
- ISO Compliance
- HIPAA Security, Privacy, & Breach Notification Rules
- GLBA
- FERPA
- GDPR, CCPA
By the Numbers
Cyber risks are not just a looming issue; they can happen at any point, which is why you need to monitor your processes and systems and strive to maintain compliance. Now's the time to take control of your cyber risk processes.
35%
of all cyberattacks were ransomware, an 84% increase from the prior year.
1,265%
rise in phishing attacks, largely driven by the rapid growth and misuse of GenAI technologies.
277 days
is the average time it takes security teams to fully identify and contain a data breach.
Industries We Serve
Learn more about each of our core practice areas and the services we offer to help you maintain compliance and safeguard your sensitive data, employees, and organization.
Risk & Compliance Insights
Curated content related to current risk and compliance issues and how we can help provide guidance.


















