
CMMC Simplified: Best Practices for Preparing
- Published
- Oct 15, 2025
- Topics
- Share
Protecting information from cybercriminals and unintended loss is a priority for every enterprise, especially the U.S. government. To further limit the impact that cybersecurity events can have on national security and the economy, the U.S. Department of Defense (DoD) modernized its cybersecurity requirements by commissioning the Cybersecurity Maturity Model Certification (CMMC).
But what is CMMC, and who does it affect? If you're a participant in the DoD's supply chain as a prime or subcontractor, this article will break down the basics of what the CMMC is and how best to prepare for compliance.
Key Takeaways
- The Cybersecurity Maturity Model Certification (CMMC) is a DoD initiative that standardizes cybersecurity requirements for participants in the Defense Industrial Base (DIB).
- There are three levels of certification, each with increasing cybersecurity practices: Level 1 for basic FCI protection, Level 2 for addressing CUI with NIST SP800-171 requirements, and Level 3 for advanced measures with NIST SP800-172.
- To prepare for CMMC compliance, participants should identify relevant IT systems, evaluate their maturity level, perform required self-assessments, create a Security System Plan (SSP), and consult third-party professionals.
What Is CMMC?
The CMMC is the security standard set by the DoD to make sure participants operating within the DoD supply chain, known collectively as the Defense Industrial Base (DIB) sector, protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) received while doing either direct or indirect business with the DoD.
With more than 300,000 direct and subcontracting participants working within the DIB, there are many opportunities for risk events to affect national security. The CMMC encourages, and will eventually require, uniform cybersecurity protection throughout the DIB. The DIB must implement the required cybersecurity maturity level of the CMMC’s requirements, save for participants that produce only commercial off-the-shelf products.
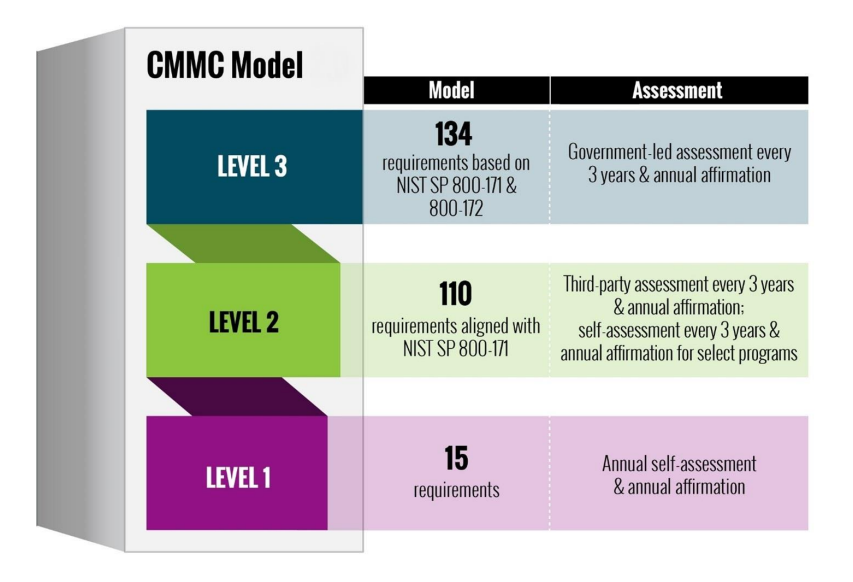
Three levels of the Cybersecurity Maturity Model Certification
Level 1: Focuses on protecting FCI and includes basic cybersecurity practices aligned with FAR Clause 52.204-21.
Level 2: Addresses CUI and incorporates 110 security requirements from NIST SP800-171 Rev 2, requiring a higher level of cybersecurity practices.
Level 3: Protects the most sensitive information and adds practices from NIST SP800-172, with DoD-approved parameters, focusing on advanced cybersecurity measures.
What Does CMMC Entail?
The DoD will assign DIB participants one of the three maturity levels for required CMMC compliance, upon which the participant must become certified at that level via self-assessment and affirmation (Level 1 and 2), and accompanying third-party audit by an authorized CMMC assessor (Level 2 and Level 3). The level assigned is determined by the type and nature of information in the bid for those directly engaged in pursuing contracts or, if serving as a subcontractor, flowed down from the participant’s prime contractor.
Key Steps to Transition to CMMC
If you are new to participating in the DoD supply chain, get a jump start on the CMMC program requirements. The following steps will assist you in preparing to work as an approved supplier, easing the transition to CMMC when required and facilitating the required audit.
- Identify the IT system(s) that will be in scope. CMMC is applied to IT systems, not the organization itself.
- Acquire a CAGE code, as it is the unique identifier for suppliers, government or defense agencies, and various organizations.
- Estimate your maturity level by assessing your data footprint and whether you will likely obtain federal contract information and CUI.
- Evaluate the likelihood of passing the Level 1 and Level 2 assessments for the systems in scope. There are specific requirements for each level.
- Perform a CMMC Level 1 and Level 2 (if applicable) self-assessment. Obtain the assessment by signing up on the DoD’s Supplier Performance Risk System (SPRS) and selecting the appropriate CAGE code for your organization.
- Create a Security System Plan (SSP) and a Plan of Actions and Milestones (POA&M) that document the state of your current network and how you plan to achieve 100% compliance.
- Submit your assessment, scoring, SSP, and POA&M to the SPRS.
Partnering for CMMC Success
CMMC helps the DoD standardize security from top to bottom in its supply chain, thereby protecting confidential information in the process. CMMC certification is poised to become the absolute requirement for obtaining and keeping DoD contracts. Do not wait to get started. The DoD has a CMMC frequently asked questions page where you can find more specific information about the process and how it will affect enterprises.
If you already do business with the DoD, you are likely familiar with the current cybersecurity requirements under NIST. Regardless, partnering with an independent third-party or a CMMC consultant helps complete the process correctly and efficiently. To learn how our CMMC services can help you transition and remain compliant with CMMC, contact us below.
What's on Your Mind?
Start a conversation with Michael












