
Six Ways To Improve Your Organization’s Cybersecurity Posture
- Published
- Aug 12, 2021
- By
- Rahul Mahna
- Share
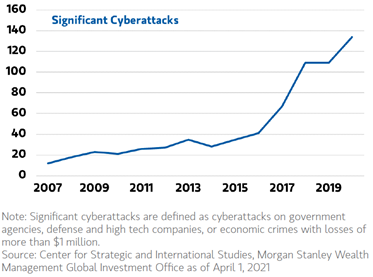
Cybersecurity attacks are growing and evolving in techniques and severity. Attackers are using the “best bang for the buck” technique in their approach to spreading malicious code. They realized if they can impact a supply chain, they can get the maximum exposure to potential payers and/or get the most monetary return because of the severity of the impact of a supply chain breach. Examples can be seen across supply chain industries, as well as other industries. Recent newsworthy examples include the Colonial Pipeline (oil and gas), JBS Holdings (food processing), SolarWinds (software), Kaseya (software) and Synnex (product distribution).
To offset the chances of such an attack, there are six key measures organizations can implement to enhance their security posture.
- Multiple Authentication Requirement
- Enable multi-factor authentication for all company-used applications and assets.
- Having these features enabled prevents attackers from stealing a password to an account and immediately signing in to it.
- Vulnerability Scans
- Perform yearly penetration tests on systems.
- A yearly assessment of the strength and protection of IT infrastructure helps keep the company constantly up-to-date on all security patches for servers and workstations.
- Training
- Enroll employees in monthly cybersecurity training and awareness courses to provide access to the most up-to-date knowledge in regards to cybersecurity.
- The end-user is one of the most attractive assets to an attacker as there always is a chance for human error.
- With constant training and awareness in security-centric ideas and practices, the room for human error decreases.
- Dark Web Scans
- Companies should monitor their email domain on the dark web to stay up-to-date on any compromises that occur on the web.
- The Colonial Pipeline attack occurred because a former employee’s credentials were found on the dark web and were still active in the company. This allowed the attackers to bypass all the security systems put in place. Monitoring the dark web and removing/disabling old credentials can help prevent such occurrences.
- Make a Plan
- Formulate a business continuity plan (BCP)/disaster recovery plan (DRP) on all systems to be prepared for attacks such as ransomware or from natural disasters.
- Having a BCP/DRP in place can help reduce the downtime in a disaster. Backing up servers and workstations to devices designed for BCP/DRP can help business continue by creating a virtual machine of the server on the cloud. This allows business to continue as normal while the physically affected server can be fixed from the disaster that occurred.
- Assess Risk
- As hackers evolve their techniques, a well-run IT organization needs to have their security profile and risk assessed on an annual basis.
- Using frameworks like National Institute of Standards and Technology (NIST) or Fir$T Look implemented by a third party can provide an independent review of the current cyber posture and where the financial and security risk is as compared to peers and industry benchmarks.
What's on Your Mind?
Start a conversation with Rahul
Receive the latest business insights, analysis, and perspectives from EisnerAmper professionals.











