Privileged Access Management: Why Organizations Need to Consider a Strategy to Enhance Data Protection
- Published
- Aug 18, 2022
- By
- Gaini Umarov
- Share
Introduction
A challenging area of focus many organizations face in today’s complex digital era is protecting data and preventing data leaks, particularly with the proliferation of sensitive personal information or proprietary corporate data maintained across a diverse technology and services ecosystem residing on-premise and in the cloud. While users are often empowered to create, store, and share information among services and devices, this complexity and difficulty of securing the data is taxing. Furthermore, data leakage takes many possible avenues including accidental oversharing of information outside the organization, willful misconduct by employees placing data in locations not sanctioned by information technology (IT) teams, or more dubious data theft scenarios with malicious intent by bad actors. All scenarios magnify the risk of data exposure when privileged levels of systems and application access levels are compromised. Consequently, the organization is handicapped and must seek measures to effectively recover from possible loss and exposure. To combat this challenge, organizations must consider an effective privileged access management (PAM) strategy and action plan as part of their overall information security program to mitigate the risk from this business challenge.
PAM Overview
So, what exactly is PAM? PAM is a protocol that consists of applying disciplined cybersecurity strategies and technologies to exert control over “privileged” or elevated access and permissions for users, accounts, processes, applications, and systems across an IT environment. PAM is an integrated and layered approach to security to enable a more robust security model and maximize the protection of sensitive information. PAM allows chief information security officers (CISOs) and chief information officers (CIOs) to protect an organization from internal and external threats and reduce compliance exposure. From a system administrator perspective, PAM will allow them to discover, manage, audit, control and store privileged accounts to reduce risk and enhance compliance.
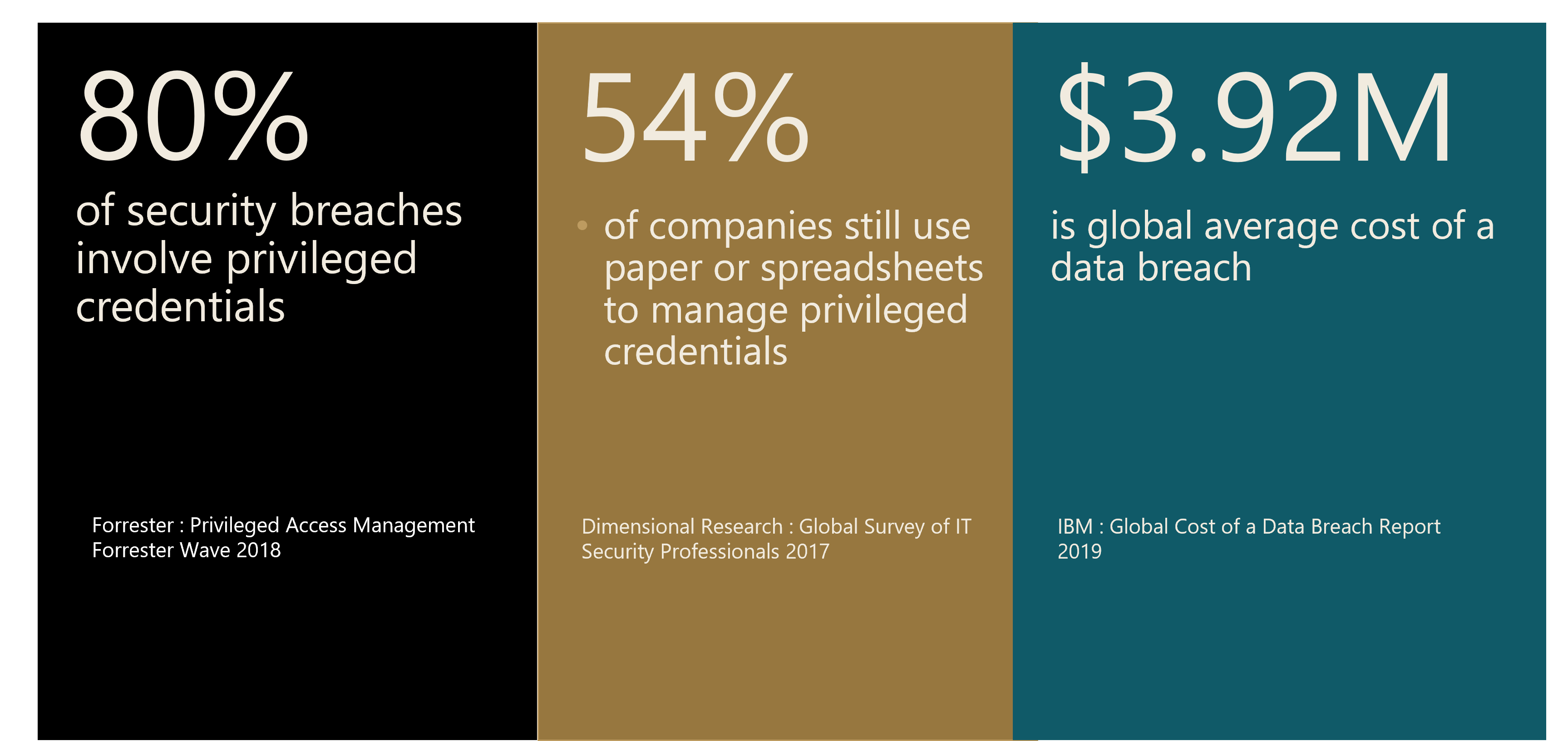
You may be thinking, why wouldn’t an organization simply implement stricter rules for passwords, increase access controls and apply more auditing oversight of system administrator level accounts? Unfortunately, applying a PAM approach is not a simple undertaking in today’s complex and dynamic environment. There exist multitudes of privileged accounts utilized within modern business environments and the variety of privileges that exist throughout many of the various business operations and services performed by the enterprise further complicate matters. Considering technology is an inherent component of every nuance of how businesses are operating -- front office functions through to the business back office combined with a dynamic and evolving nature of modernized systems -- the challenges are difficult to address with yet another layer of technology. Privileged accounts persist in various forms including 1) user-specific administrative or elevated level accounts (i.e., local or domain administrator or similar superuser), 2) non-interactive accounts such as service-level-oriented backup and restoration privileges, application-focused to help manage, administer, and configure certain application software, or embedded in artificial intelligence (AI), internet of things (IoT) devices, and/or robotic process automation (RPA), or 3) highly specialized accounts for enabling direct access to operating systems, databases, or various application-specific uses. The variety of uses of privileged accounts is boundless. According to CyberArk, which provides PAM solutions, “it is estimated that [privileged accounts] typically outnumber employees by three to four times”.1
This pervasive nature of privileged identities throughout the digital ecosystem increases the overall attack surface for organizations. Thus, if a privileged account is not properly protected, the account can either be a direct or indirect culprit in the compromise and data exposure for a company. In addition, when providing compliance for the E.U. General Data Protection Regulation (GDPR), the Payment Card Industry (PCI), Health Insurance Portability and Accountability Act (HIPAA), National Institute of Standards and Technology (NIST) and other regulation to secure privileged access within your environment, a PAM adoption strategy is highly recommended.
How Organizations Can Execute an Effective PAM Strategy
With a thoughtful PAM strategy coupled with a disciplined execution approach, an organization can positively improve the protection of its sensitive information and mitigate the risk of harm to business operations. As a takeaway, a few recommended leading practices for an effective PAM strategy include the following:
- Enable multi-factor authentication (MFA) to add a layer of protection to the login process for all accounts. This feature will provide the tremendous benefit of limiting the threat of unauthorized parties stealing or leveraging any account, particularly privileged accounts, and doing harm.
- Apply a least-privileged access or restricted access to complete task approach for accounts to minimize exposure from malicious attacks, improve auditability and reduce overall risk and impact to the overall business operations and technical environment. Furthermore, consider the use of application whitelisting or an allowed list to provide an additional layer of protection to access a particular system privilege, service, or function.
- Protect privileged credentials for use with third-party applications for on-premise or cloud-based solutions through native or third-party key vault solutions.
- Eliminate use of hardcoded credentials to be used in any system, application interfaces or related systematic login processing.
- Perform periodic vulnerability assessments and at least annually conduct penetration tests to identify improperly protected or suspicious accounts on the IT infrastructure.
- Train all employees routinely on cybersecurity practices and awareness to have the most current and relevant information on account protection and use.
- Regularly and routinely review audit trails and logs for suspicious behavior and activities performed by privileged user accounts.
Conclusion
Attention to PAM is percolating as a top-of-mind matter for scores of business and IT executives to address. With the ongoing proliferation of ransomware attacks on the rise and breach investigations increasingly revealing unprotected privileged accounts at the root of many of the disastrous security breaches, robust management of privileged identities is paramount. As organizations evolve and expand their digital footprints, inherently taking stock of privileges and the power that these accounts have upon the business necessitates that these identities must be effectively managed.
1https://www.cyberark.com/what-is/privileged-access-management/
Our Current Issue Q3: 2022
What's on Your Mind?
Start a conversation with Gaini
Receive the latest business insights, analysis, and perspectives from EisnerAmper professionals.